Describe in Your Own Words How Polyalphabetic Substitution Works
If you are describing methodology please describe it in sufficient details so that by following it anybody can reach the same result without additional help from you. Last week we worked on monoalphabetic substitution ciphers -- ones which were encoded using only one fixed alphabet hence the Greek root mono meaning one.

Cryptology Vigenere Ciphers Britannica
When the prices of a good goes up people are more likely to buy a substitution for example if apples price go up then people buy bananas.
. The plaintext alphabet on his cipher disk was in order and included the digits 1 through 4 for. The general name for this approach is polyalphabetic substitution cipher. His system involved writing the ciphertext in small letters and using capital letters as symbols called indicators to indicate when the substitution changes now and then through a message.
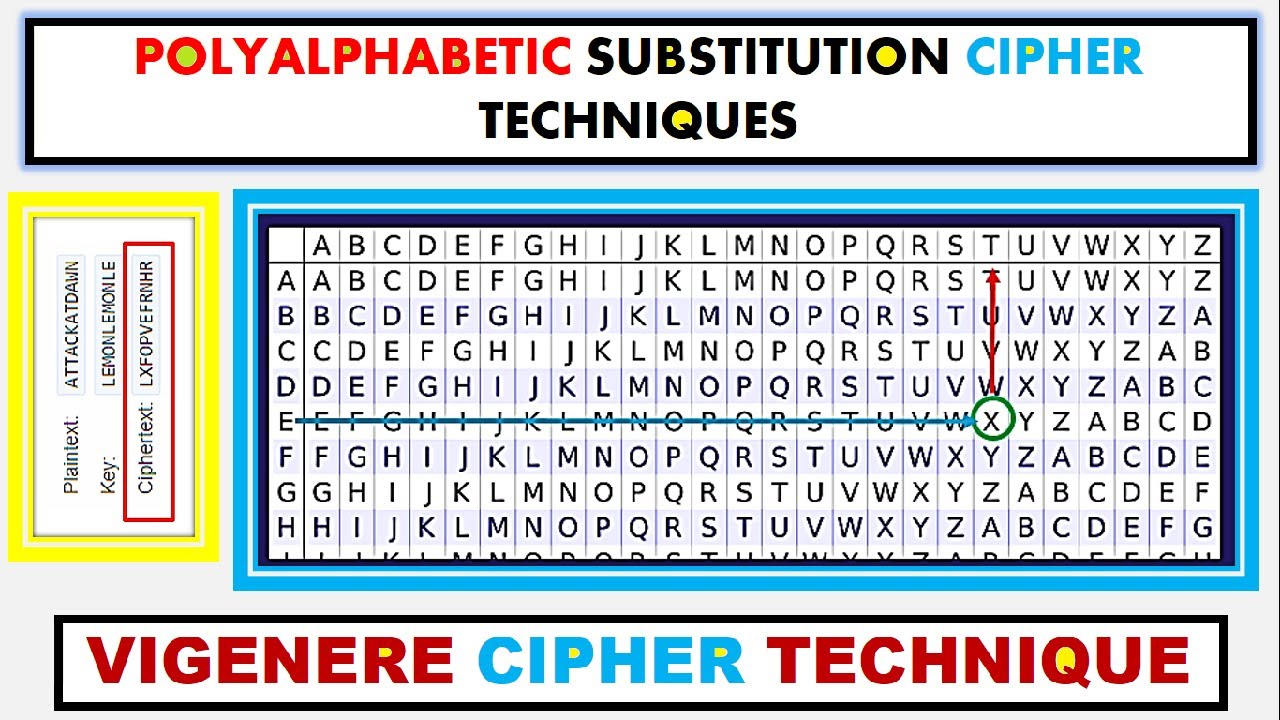
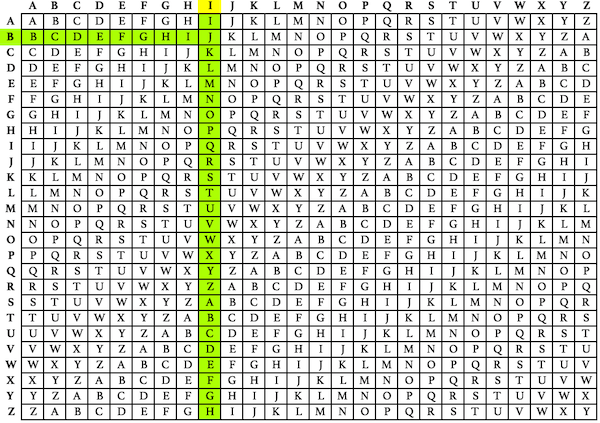
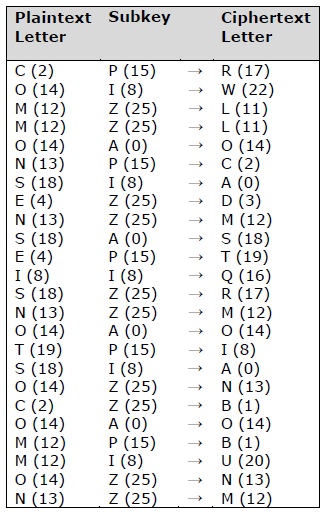
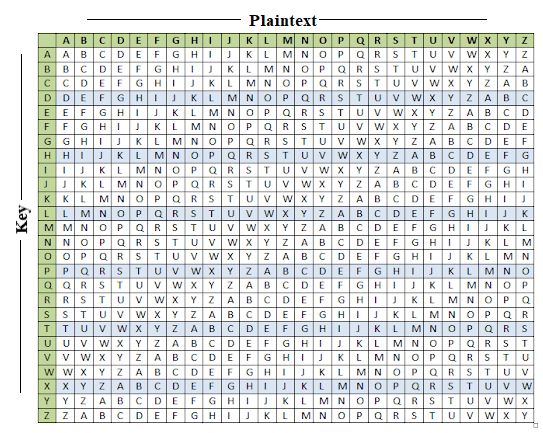
Polyalphabetic Cipher is a substitution cipher in which the cipher alphabet for the plain alphabet may be different at different places during the encryption process. The encryption of the original text is done using the Vigenère square or Vigenère table. Total 40 Choose the best one.
List and describe three causes for a shift in the demand curve. Hv ufe fh kar karvedrh vu pfkarpfkdlh fer fivnk erfmdkz karz fer svk lrekfds. Each plaintext character is replaced by another letter.
5 Describe the importance of auditing and what should be audited in network. Polyalphabetic substitution ciphers were invented by an artist philosopher and scientist Leon Battista Alberti. What does polyalphabetic mean.
The more correct guesses youll make the more closer you will get and eventually youll be able to crack the final mono-alphabetic code. Return encrypt text key reverse_operationTrue. Reason must be in your own.
Substitution ciphers are a part of early cryptography predating the evolution of computers and are now relatively obsolete. Part I Each 4 Pts. As you saw especially when the spaces between words are still there these are fairly easy to break.
Polyalphabetic cipher is any cipher based on substitution using multiple substitution alphabets. A way of substitution is changed cyclically and it depends on a current position of the modified letter. The earliest form of polyalphabetic cipher was developed by Leon Battista Alberti by 1467.
2 Describe methods of account management SSO time of day logical token and account expiration. 4 Describe in detail how polyalphabetic substitution works. A polyalphabetic cipher is any cipher based on substitution using multiple substitution alphabets.
View 04-Polyalphabetic-Substitution-Ciphers-Part2-Playfair-Cipherpptx from ARTF 145 at Wichita State University. Other than Substitution cipher Transposition cipher or Vigenѐre cipher that you can use to encrypt and decrypt a certain message. If the plain text original message is considered as the string of bits then the substitution technique would replace bit pattern of plain text with the bit pattern of cipher text.
Monoalphabetic cipher is one where each symbol in plain text is mapped to a fixed symbol in cipher text. Polyalphabetic Substitution Ciphers March 18 2004 About the Ciphers. For example instead of this.
A stream cipher is a polyalphabetic cipher if the value of key does depend on the position of the plain text character in the plain text stream. Describe the substitution effect in your own words and give an example. Using several substitution alphabets in turn see multiple-alphabet cipher progressive-alphabet cipher vigenère cipher.
Higher score closer the original plaintexts letter frequency is to regular Englishs letter It uses a simple form of polyalphabetic substitutionA polyalphabetic cipher is any cipher based on substitution using multiple substitution alphabets The encryption of the original text is done using the Vigenère square or Vigenère table. It includes autokey Playfair Vigenère Hill one-time pad rotor and Enigma cipher 6. The table consists of the alphabets written out 26 times in different rows each alphabet shifted cyclically to the left compared to the previous alphabet corresponding to the.
The next two examples playfair and Vigenere Cipher are polyalphabetic ciphers. You should follow PEP8 the official coding style guide of Python. A substitution cipher is a type of encryption where characters or units of text are replaced by others in order to encrypt a text sequence.
Based on your cipher text you need to make assumptions and replace each letter one by one and then analyze the final result to be sure that your answer makes sense. Return encrypt textkeyreverse_operationTrue You should put a space after every comma separating a list of parameters like this. The relationship between a character in the plain text and the characters in the cipher text is one-to-one.
3 Identify the differences among user group and role management. It is a simple substitution cipher. If you are describing methodology please describe it in sufficient details so that by following it anybody can reach the same result without additional help from you.
Polyalphabetic Substitution CipherPart 2- Playfair Cipher Learning Objectives. Hv ufe fh karz fer lrekfds karz fer svk fivnk erfmdkz Fmirek Rdshkrds. In a decimation cipher A always represents itself.
Describe Block Cipher in your own words and explain working of one block cipher algorithms currently available. Please write justification in your own words avoid cut and paste or merely copying the sentences from references. Subject Cryptography and.
Information and translations of polyalphabetic in the most comprehensive dictionary definitions resource on the web. It includes additive multiplicative affine and monoalphabetic substitution cipher. Another way to improve on the simple monoalphabetic technique is to use different monoalphabetic substitutions as one proceeds through the plaintext message.
Caesar cipher ROT13 Polyalphabetic Brute Force. Please provide reason of your choice in a few sentences or reasons not choosing the other choices. Monoalphabetic ciphers Our examples of the permutation shift decimation and affine ciphers were monoalphabetic ciphers that is every letter was replaced by the same letter each time.
Substitution technique is a classical encryption technique where the characters present in the original message are replaced by the other characters or numbers or by symbols. All these techniques have the following features in common. Polyalphabetic substitution definition a system of substitution that mixes together a number of cipher alphabets in a cryptogram so that each plaintext letter is represented by a cipher that repeatedly changes.
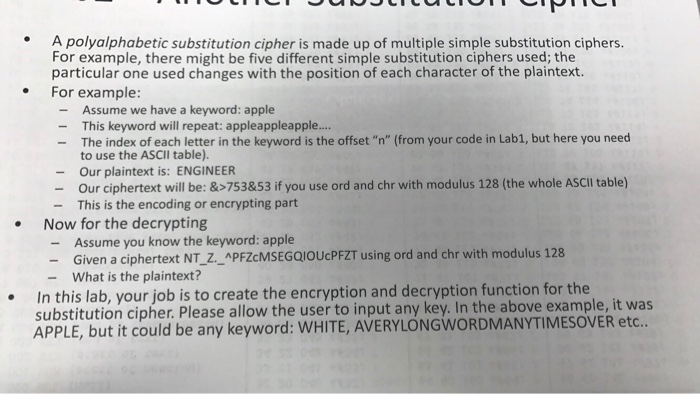
Solved A Polyalphabetic Substitution Cipher Is Made Up Of Chegg Com
The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher
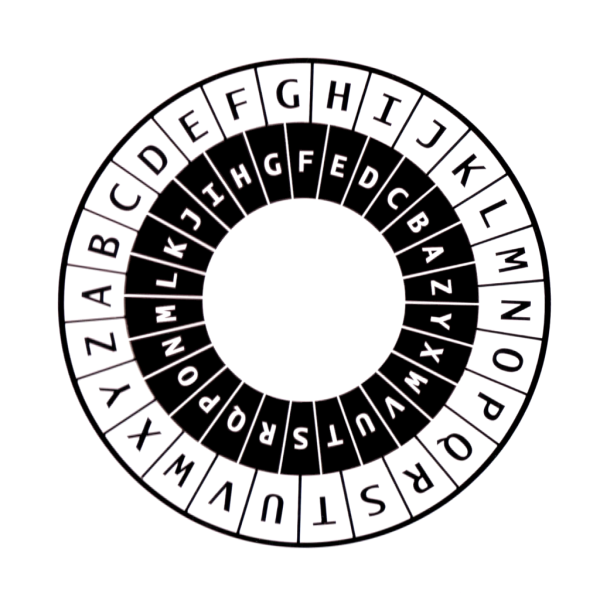
5 0 The Mechanization Of Ciphers

Solved Case 3 Vigenere Cipher Decryption Vigenere Cipher Is Chegg Com

Polyalphabetic Substitution Ciphers Crypto Corner
Vigenere Cipher Automatic Solver Boxentriq

Polyalphabetic Substitution Ciphers Crypto Corner
The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher
Types Of Cipher Learn Top 7 Various Types Of Cipher In Depth
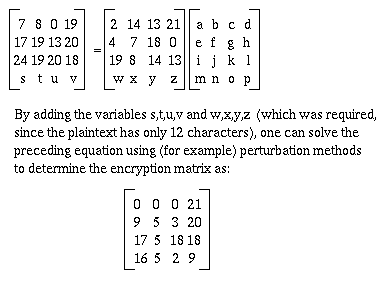
Cryptology I Homework 1 Mono And Poly Alphabetic Ciphers

Cryptanalysis Of Polyalphabetic Cipher Such As Vigenere Cipher Xray Pixy Youtube

Polyalphabetic Substitution Ciphers Crypto Corner
Polyalphabetic Substitution Ciphers Crypto Corner
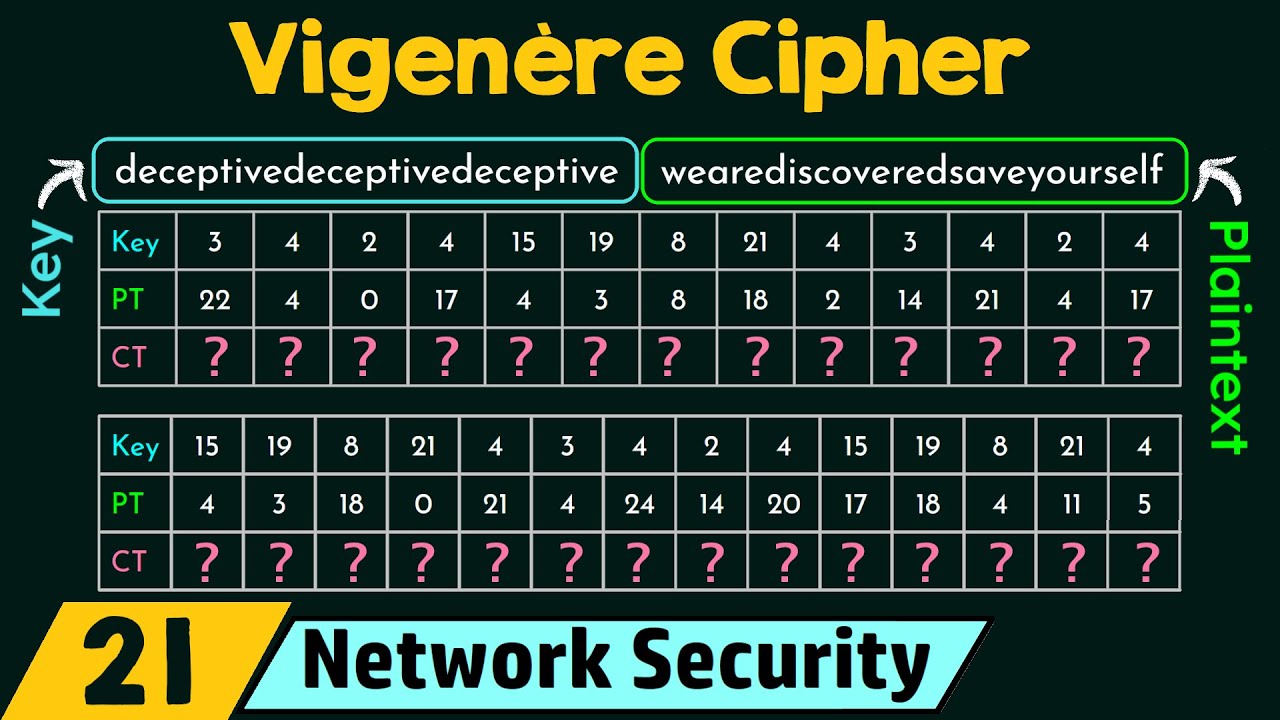
Is A Polyalphabetic Substitution Cipher

How Much Do You Know About The Vigenere Cipher Ibm Z And Linuxone Community


Comments
Post a Comment